Ransomware is similar to other malware in that it installs itself on a computer and runs in the background without the user’s knowledge. But unlike malware that hides and steals valuable information, ransomware doesn’t hide. As soon as ransomware has locked a user’s machine and/or encrypted files, it notifies the user of its presence to make the ransom demand.
An Example of How Ransomware Works
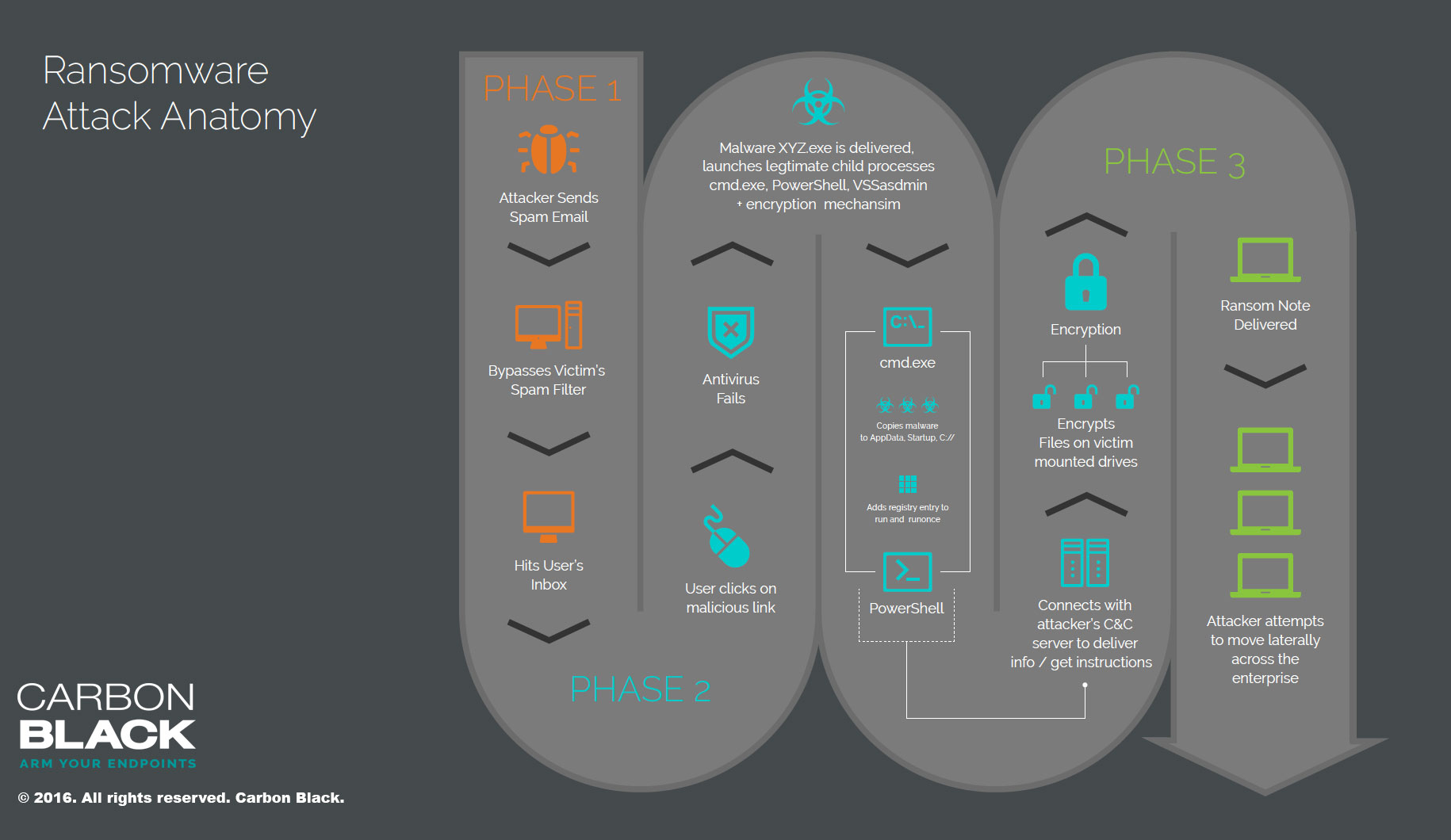
Here’s an example of the stages of a “Locky” attack originating from a spear-phishing email. (Click the image to enlarge.)
1. End user receives an email that appears to be from their boss.
It contains a URL to a SaaS application such as Salesforce, Workday or ZenDesk.
2. The link opens a browser window and directs the user to a website that seems legitimate.
It’s actually a landing page for an exploit kit hosted in a .co.cc top level domain (TLD).
3. Upon loading the page, the web server hosting the exploit kit begins communicating with the victim machine.
The server sends requests about versions of software such as Java to find a vulnerable version for which the kit has an exploit.
4. When a vulnerable version is confirmed, the kit attempts to exploit the vulnerability.
Once successful, the exploit kit pushes down a malicious .EXE file – let’s call it “ransomware.exe.” The malicious binary on the victim machine then attempts to execute.
5. From this beachhead, the binary spawns child processes, including vssadmin.exe (shadow copy), to delete existing shadows on the victim machine and create new ones to hide in.
The attacker does this to limit the possible recovery of files by the victim using Shadow Copies that Windows stores on a system.
6. The binary also creates a powershell executable to propagate copies of itself throughout the filesystem.
The executable also searches the filesystem for files of specific extensions and begins to encrypt those files.
7. The powershell.exe child process creates three copies of the originating malware binary, first in the AppData directory, next in the Start directory, and finally in the root C:\ directory.
These copies are used in conjunction with the registry modifications to restart the malware upon reboot and login events.
8. After encrypting the victim’s files, the malware sends the encryption key and other host- specific information back to the command-and-control server.
9. The server then sends a message to the victim.
This could be a simple “alert user of encryption and directions on paying us.” It could also include directions that result in downloading additional malware, which enables the attacker to steal credentials from the victim as well.
To amplify the victim’s distress, ransomware often includes a countdown clock with a deadline for paying the ransom – or else the decrypt key will be destroyed, eliminating any chance of recovery.
Paying the ransom often means the attacker will unlock the victim’s machine or provide the key to decrypt files. However, it rarely means the originating malicious binary, “ransomware.exe” in the case above, has been removed. That will require IT and SecOps support.
And the attack doesn’t necessarily end there. Attackers often load additional malware on a user’s machine, allowing them to harvest personal information, intellectual property, and credentials to sell for additional revenue.
• PG & D • WORLDWIDE • DIGITAL • NET • IT